YouTube Hacker Performs Crypto Hack Worth $2 Million
- By: Sean van der Merwe on February 7, 2022
- Categories: Cryptocurrency

Crypto hardware wallets are known for their strong security and are often touted as the safest way to store your cryptocurrencies. However, Joe Grand, took to YouTube to showcase the crypto hack of the century, when he retrieved $2 million in Theta coins from a secured cryptocurrency wallet.
The Story Behind the Crypto Hack
In 2018, Crypto investor, Dan Reich, and a friend invested $50,000 in an up-and-coming cryptocurrency, called Theta (worth 2 cents at the time). It was transferred to a Trezor hardware wallet for safe-keeping and password protected for safety.
When Theta surged to $15 per coin in 2021, Reich requested that his friend sell their holdings and cash in on the now $2 million investment. Unfortunately, his unnamed co-investor forgot the password for the device and after 12 incorrect PIN guesses, they stopped trying. If had gone on to enter it incorrectly 16-times, it would have resulted in all the data being erased.
Unlike centralised currency, crypto users have no trusted middleman (bank) to turn to in the case of lost passwords or account retrievals. If you lose your password, you lose access to the private key on the device. This key, in turn, is used to authorise currency transfers. In simple terms, if you lose your private key, you lose your investment. This isn’t an uncommon occurrence in crypto circles either.
In an act of desperation, Reich turned to the internet to find an ethical hacker who could break into his device for him and retrieve the funds. He reached out to Joe Grand, a reformed juvenile delinquent hacker turned electrical engineer and inventor. Joe has now turned his hacking “super-power” into a business that helps those who find themselves in similar situations to Dan.
The Mechanics of the Crypto Hack
Joe was ecstatic to be given the opportunity to crypto hack a device that was believed to be un-hackable. The challenge was an opportunity that he just could not turn down. So, tying up a liability contract absolving Joe of any potential loss in the crypto hacking process, he set about his mission. It eventually involved a 12-week testing phase, whereby he worked methodically to figure out how to unlock the digital vault in similar wallets.

Joe’s crypto hack test devices – Image courtesy of YouTube
Unlike the movies, hacking is a slow and complex procedure. You are basically forcing hardware and software to behave in a way that it is not designed to. The trick is to get the program to misbehave in a way that you can control. This procedure is called “Fault Injection.”
After almost 3 months, Joe finally cracked a tester wallet. He said:
“We are basically causing misbehavior on the silicon chip inside the device in order to defeat security. And what ended up happening is that I was sitting here watching the computer screen and saw that I was able to defeat the security, the private information, the recovery seed, and the pin that I was going after popped up on the screen.”
He realized that certain devices with outdated firmware would copy the secret information he was after to the RAM on the device upon powering up. The secret to retrieving the information involved glitching the start-up process and copying the RAM to his computer before the data was moved back to the flash. The glitch would fool the chip into thinking that Joe had rightful access to the RAM, even though he didn’t. However, it was far from a simple process.
Down to The Deed
Once Grand had figured out the key to the crypto hack, he contacted Dan Reich and organized for him to fly in with the wallet so that they could give the hack a go. Once Dan had arrived, they spared no time getting down to business.

Joe and Dan during the crypto hack – Image Courtesy of YouTube
The preparation involved:
- Carefully taking the chipset and circuit board out of its plastic container.
- Applying chemicals to the chip to remove its protective anti-static coating.
- Delicately removing two capacitors, making the chip more responsive to the glitches.
- Soldering connectors to the chip.
- Connecting hacking devices to the circuit and then to his PC.
Once everything was connected, they initiated the start-up and put into effect the glitch attack. The procedure would run a loop of different glitch offsets until it found the one that successfully compromised the security.
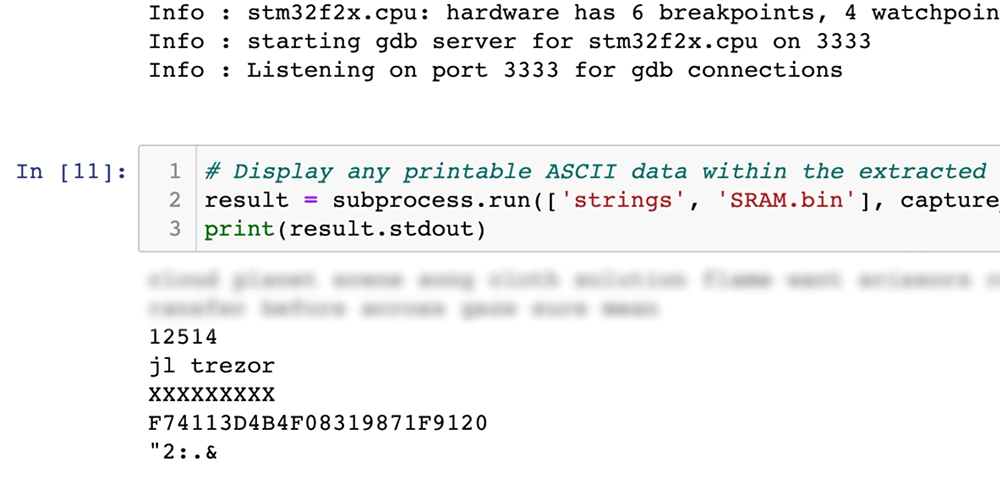
RAM data revealing the pin for the Trezor Wallet – Image courtesy of YouTube
After 3 hours and 19 minutes, the crypto hack was successful, and the RAM was copied to Joe’s PC. He scrolled through the code on this desktop and there it was! A 5-digit pin for the device – 12514. Dan’s relief was evident, and he was able to access his assets immediately.
Trezor’s Response to the Crypto Hack
Trezor was quick to respond to the video that went viral in a matter of days. They indicated that the exploit in the firmware had been fixed and that wallets could no longer copy the key and PIN to the RAM. They also left a comment in the comments section of Joe Grand’s YouTube video stating:
“Hi, we just want to add that this is an outdated exploit that is not a concern for current users and that we fixed in 2017 right after a report that we received through our responsible disclosure program. This attack requires full physical access to the device, and there is no record of any funds being compromised.”
So, it seems that modern-day investors have little to worry about when it comes to using Trezor hard wallets unless someone else finds a way to trick the system. Of course, this article serves as a great reminder to crypto investors about the importance of observing responsible hodling practices. Always use a PIN that you cannot forget, or back it up and store it in a safe place.




